The Digital Operational Resilience Act (DORA) is a significant piece of legislation passed by the European Union(EU) to enhance the cybersecurity resilience of financial institutions. The act aims to safeguard both financial entities and their customers against increasing cyber threats and potential operational disruptions, ensuring that the sector remains robust and secure in the face of evolving risks.
Explore our comprehensive guide on navigating compliance and building digital resilience – Read the Full blog Now!
Our expert team is here to guide you through the DORA readiness process, helping your institution enhance operational resilience while staying aligned with regulatory requirements. By addressing DORA’s complexities, including third-party risk management and resilience-building, we empower organizations to meet compliance requirements and strengthen long-term cybersecurity defences.
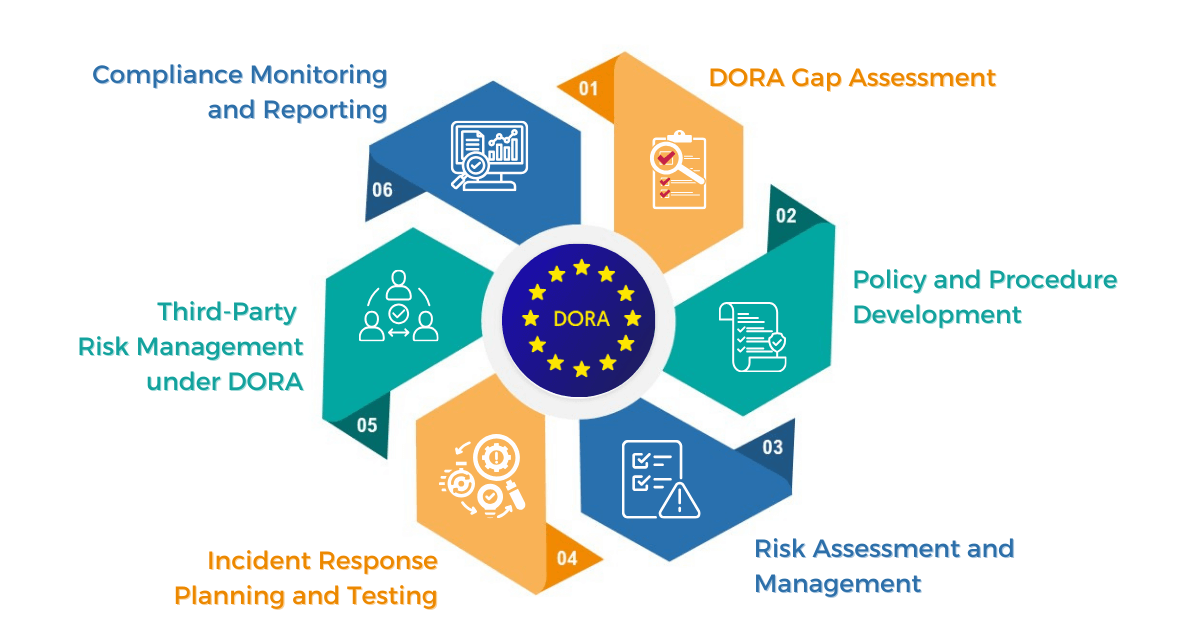




With years of specialized experience in cybersecurity and compliance, IARM offers strategic guidance to help your institution navigate DORA’s regulatory requirements. Our expertise enables you to mitigate compliance risks while enhancing the resilience of your cybersecurity infrastructure.