What You’ll Discover Inside:
The surprising reason phishing attacks still succeed—even in 2025
How to run simulations that reveal real risk, not just tick compliance boxes
Why your most trusted teams might be your biggest cybersecurity blind spots
Phishing attacks aren’t just annoying—they’re evolving, relentless, and dangerously effective. And despite growing awareness, they’re still the #1-way cybercriminals breach organizations.
Now, here’s the uncomfortable truth:
Firewalls don’t stop phishing. People do.
But only when they’ve been trained the right way.
In this guide, we go beyond definitions and dive into what makes phishing simulations meaningful— simulations that foster real behavioural change and empower your team to become the first line of defence.
Let’s dive in.

Phishing is digital deception.
Phishing is a form of social engineering where attackers impersonate trusted sources—banks, internal departments, even your CEO—to trick people into handing over sensitive information or clicking malicious links.
It usually comes in through email. But these days, it also slips in via:
And here’s the kicker: humans, not systems, are the weakest link.
That’s why phishing simulations are crucial.
Here’s the kicker: Phishing isn’t just surviving. It’s thriving.
And that’s just the visible damage.
The real problem? It’s not the attack. It’s the aftermath—compromised systems, ransomware payloads, stolen data, brand damage, and regulatory nightmares.
Gone are the days of “Dear User, please send your password.” Today’s phishing emails:
AI-powered phishing kits now produce content that feels legitimate—sometimes more convincing than real internal emails.
Your employees aren’t falling for scams. They’re falling for well-crafted, believable scenarios.
Let’s break it down:
This is where the magic happens. You can’t fix what you can’t measure.
Phishing simulations are more than training—they’re behavioral diagnostics. Done right, they reveal:
The challenge? Many simulations fall short because they feel unrealistic or too predictable.
Here’s the 5-part formula we’ve seen work across SMBs, enterprises, and startups:
Don’t blast the same fake Dropbox email to everyone. Instead:
👉 The more real it feels, the better the learning.
Forget just click rate. Start tracking:
This gives you real behavioral intelligence, not just vanity metrics.
Start with the departments most likely to be targeted:
Then, scale across the organization.
Avoid the blame game. The goal is improvement, not embarrassment. After each simulation:
Cybercriminals don’t follow a quarterly schedule—and neither should you.
Set up monthly or bi-monthly phishing tests, rotating difficulty and scenario type. Track progress over time and adapt based on behavior.
Here’s a simple blueprint that works for most companies:
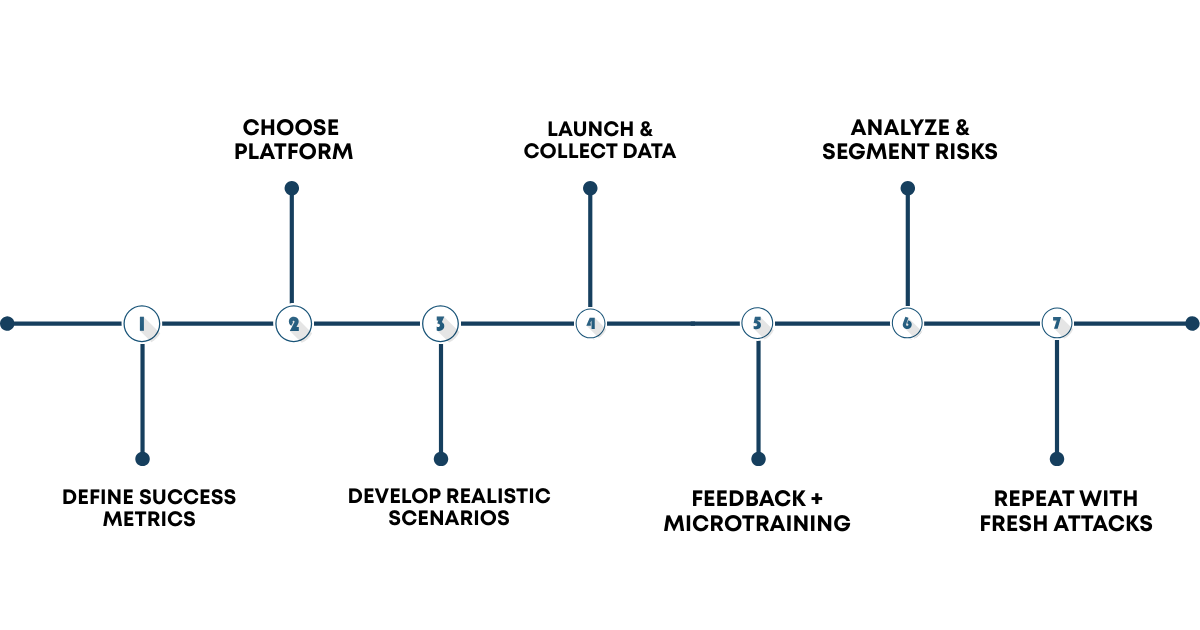
Once the data rolls in, the real work begins.
Here’s how to categorize users:
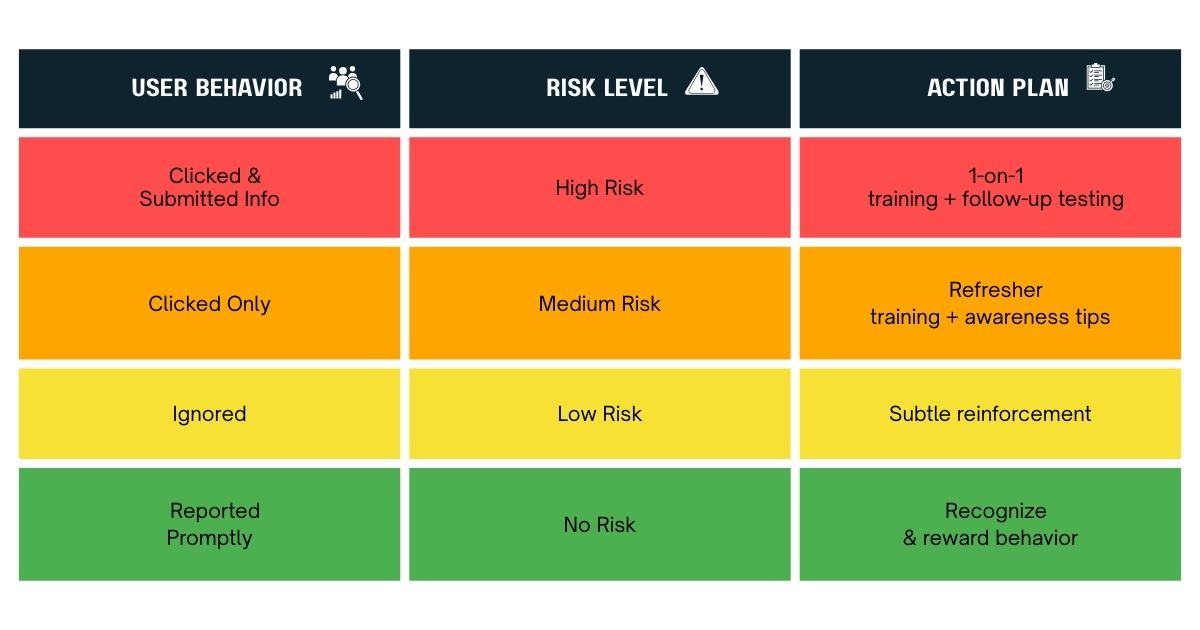
And here’s the truth: “ignored” ≠ “safe.”
Sometimes, silence hides confusion.
A strong simulation program backed by training can:
The ROI isn’t just measurable. It’s massive.
Let’s be honest: running phishing simulations on your own is tough.
That’s why we built PhishPrep—a platform designed to make phishing defense simple, scalable, and actually effective.
✅ Launch phishing simulations quickly
✅ Use real-world templates based on the latest threats
✅ Track who’s at risk—with clean, visual dashboards
✅ Auto-trigger training based on performance
✅ Align with ISO 27001, GDPR, NIST CSF & more
Whether you’re a startup or an enterprise, PhishPrep helps you fix the weakest link—before it breaks.
Ready to See Who Clicks?
The best time to run a phishing simulation was yesterday.
The next best time is now.
No pressure. No pitch decks. Just a smarter way to stop phishing before it stops you.
If you’re serious about cybersecurity, don’t just invest in firewalls and antivirus.
Invest in people. Simulate. Educate. Repeat.
Because in the battle against phishing, it’s not tech vs. humans—it’s tech plus humans, trained to think like attackers.
Make your team your strongest defense. Start with PhishPrep.