KEY HIGHLIGHTS:
Proactive Risk Identification: Recognize and mitigate security threats early in the design phase to prevent potential breaches and operational disruptions.
Regulatory Assurance: Ensure alignment with regulatory mandates by embedding security measures into your systems.
Industry-Specific Protection: Tailor threat modeling to safeguard critical sectors like finance, healthcare, e-commerce, and infrastructure from cyber threats.
Collaborative Security Approach: Promote collaboration across development, security, and compliance teams to build resilient systems.
Cost-Effective Security Management: Reduce long-term expenses by addressing vulnerabilities during the design phase, minimizing the cost of post-incident remediation
Threat Modeling Explained
Threatmodeling is a proactive approach to identifying and addressing security risks in applications, systems, and networks. It involves evaluating potential threats, vulnerabilities, and the impact they may have on an organization’s assets. By understanding how attackers may compromise systems, organizations can implement effective security measures during the development phase.
This methodology is a key component of a Secure by Design approach, ensuring that security is embedded into the architecture from the beginning rather than being an afterthought. Explore our Threat Modeling Services — leveraging STRIDE, DREAD, and MITRE ATT&CK for effective risk analysis and mitigation. Threat modeling is particularly beneficial for organizations in highly regulated sectors such as finance, healthcare, and telecommunications, where compliance and data protection are critical.
Why Secure by Design Matters
A Secure by Design approach emphasizes the importance of considering security from the very start of a project. Rather than adding security measures after a system has been built, Secure by Design ensures that security controls, risk assessments, and mitigations are incorporated throughout the development process. This proactive strategy leads to more resilient systems that can withstand potential threats and minimize vulnerabilities from the outset.
In this context, threat modeling plays a pivotal role. It enables organizations to:
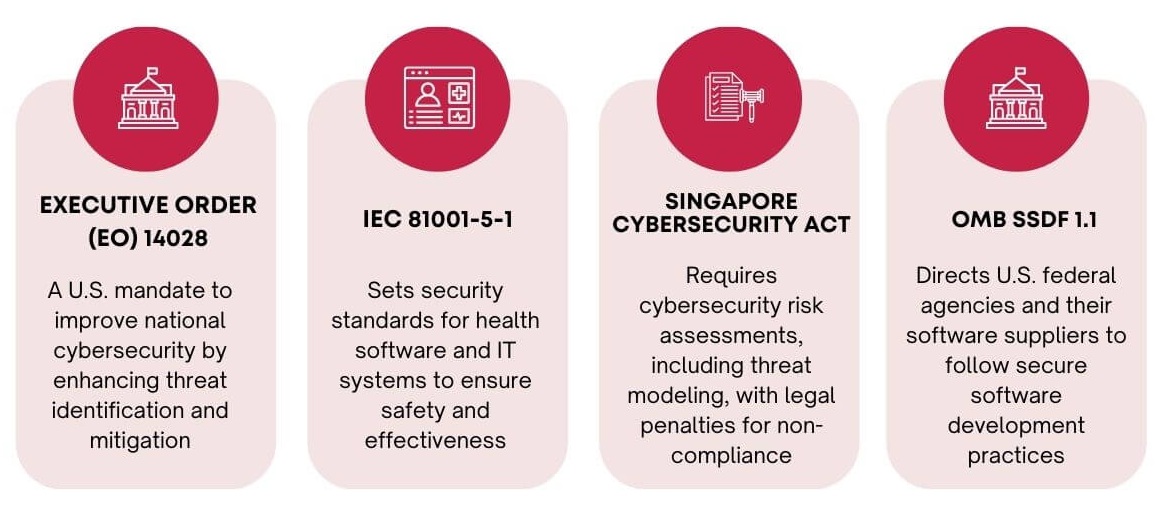
For a simplified overview of the threat modeling process, follow these essential steps:
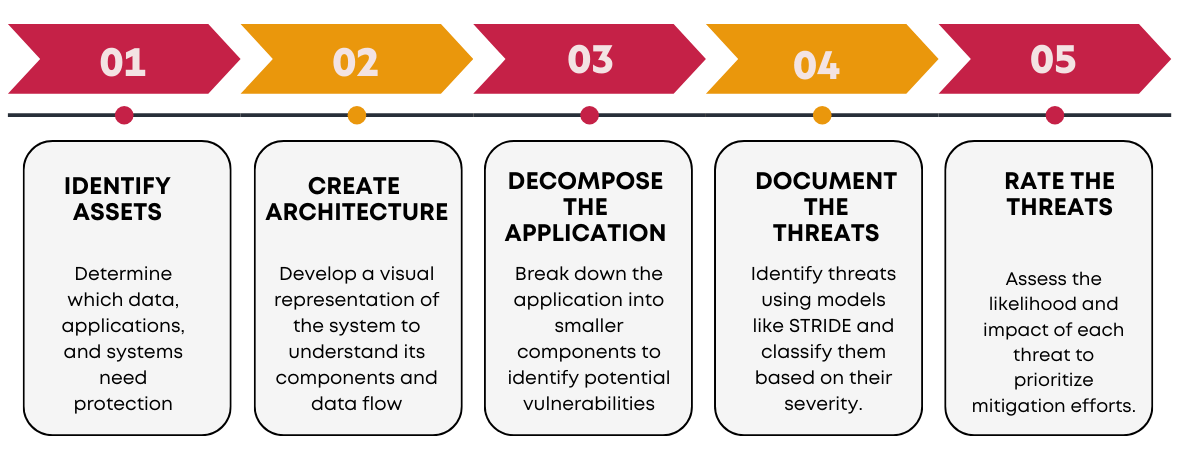
Embedding security through a Secure by Design approach with robust threat modeling is essential for organizations aiming to strengthen their cyber resilience. By identifying risks early, implementing effective controls, and maintaining compliance, organizations can mitigate potential threats and ensure business continuity.
Adopt a proactive cybersecurity posture through comprehensive threat modeling and secure your organization’s future against evolving cyber threats. Embrace security from the start and build systems designed to withstand the challenges of the digital age.