IARM’s Threat Modeling Services take a proactive, structured approach to identifying and mitigating security risks at the design stage. By integrating threat modeling early in the development lifecycle, potential vulnerabilities are uncovered before they become costly issues. Our risk-based methodology strengthens security across applications, networks, systems, IoT environments, and business processes, ensuring long-term resilience.
Our Threat Modeling Approach
IARM’s expert-driven methodology enhances security by identifying vulnerabilities proactively. Our approach includes:
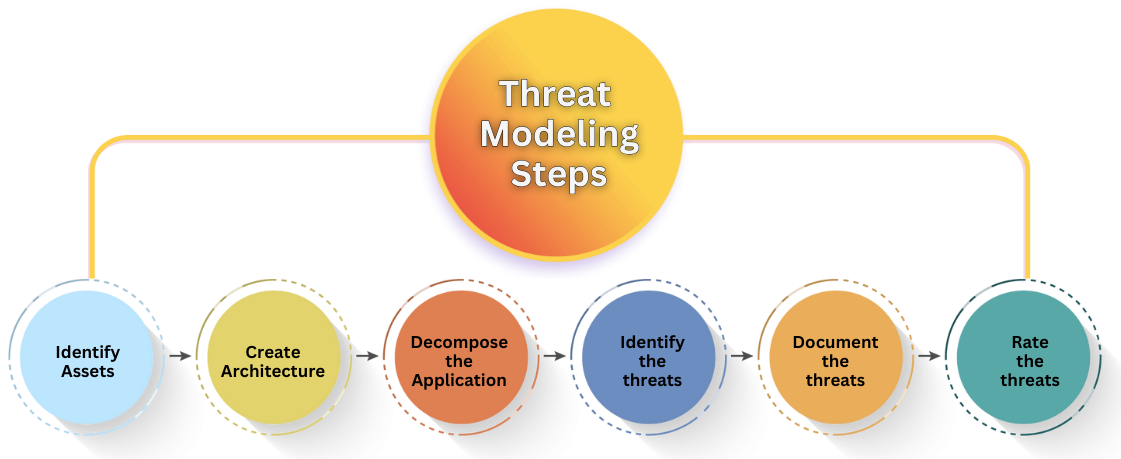
- Asset Identification – Defining critical assets, data flows, and security dependencies.
- Architectural Analysis – Mapping system components and interactions to detect vulnerabilities using security diagrams.
- Threat Identification – Using industry-recognized models like STRIDE, DREAD, and MITRE ATT&CK to analyze risks effectively.
- Threat Documentation – Maintaining comprehensive reports on risks and recommended security controls.
- Risk Assessment & Prioritization – Evaluating threats based on severity, impact, and likelihood.
- Mitigation Strategies – Implementing tailored security controls to prevent exploitation.
Regulatory Compliance & Security Mandates
Organizations must align with global cybersecurity regulations to safeguard data and operations. Threat modeling is essential for meeting compliance standards such as:
United States
Singapore
- Cybersecurity Act (2018) – Requires organizations to perform cybersecurity risk assessments, making non-compliance a potential offense.
Healthcare & Critical Systems
- IEC 81001-5-1:2021 – Defines security requirements for health IT systems, ensuring safety and effectiveness.
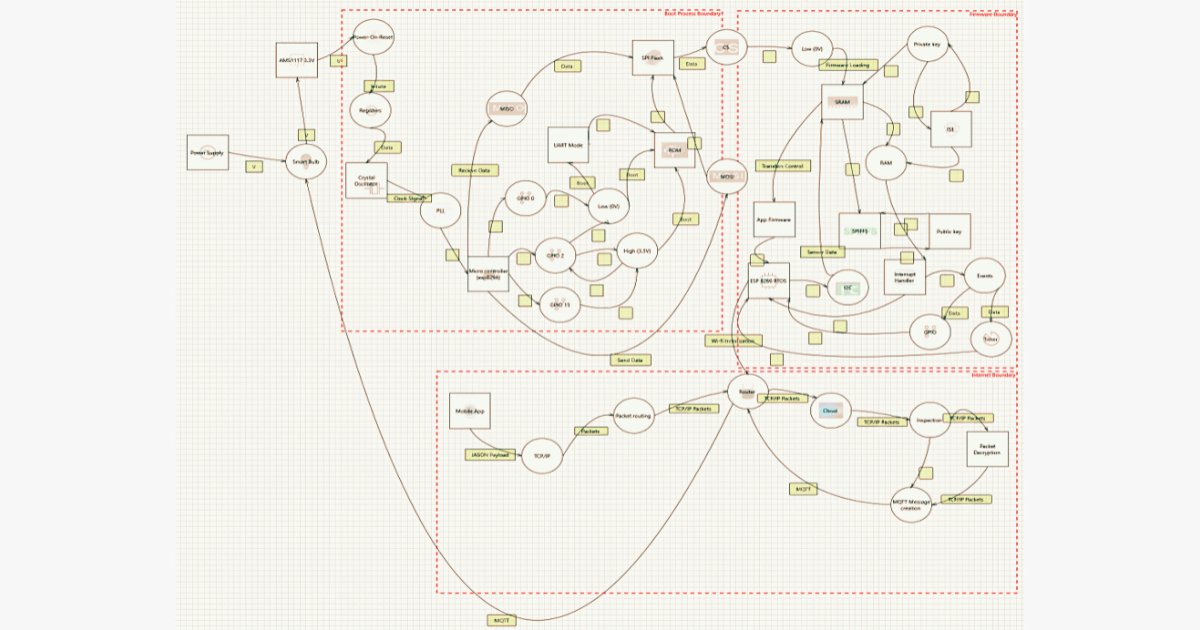
Architecture Diagram
A visual representation helps teams understand potential attack surfaces and define security threats effectively.
Why Choose IARM for Threat Modeling Services?
IARM’s threat modeling services help businesses secure their applications, networks, and critical systems through:
- Expert-Led Security Assessments – Our cybersecurity specialists conduct thorough risk evaluations.
- Industry-Specific Security Solutions – Customized threat modeling tailored for finance, healthcare, manufacturing, technology, and critical infrastructure.
- Actionable Threat Intelligence – Practical insights for effective risk mitigation and decision-making.
- Proactive Security Posture – Strengthening applications and business processes before vulnerabilities are exploited.
- Advanced Tools and Diagrams – Leveraging cutting-edge security tools and architectural diagrams to visualize and assess potential threats.
Strengthen your organization’s cybersecurity resilience with IARM’s industry-leading Threat Modeling Services. Get in touch with our experts today to safeguard your digital assets.


